See CyberVision in Action
Intuitive interface designed for security professionals

Secure Authentication
SSO integration with MFA support for maximum security
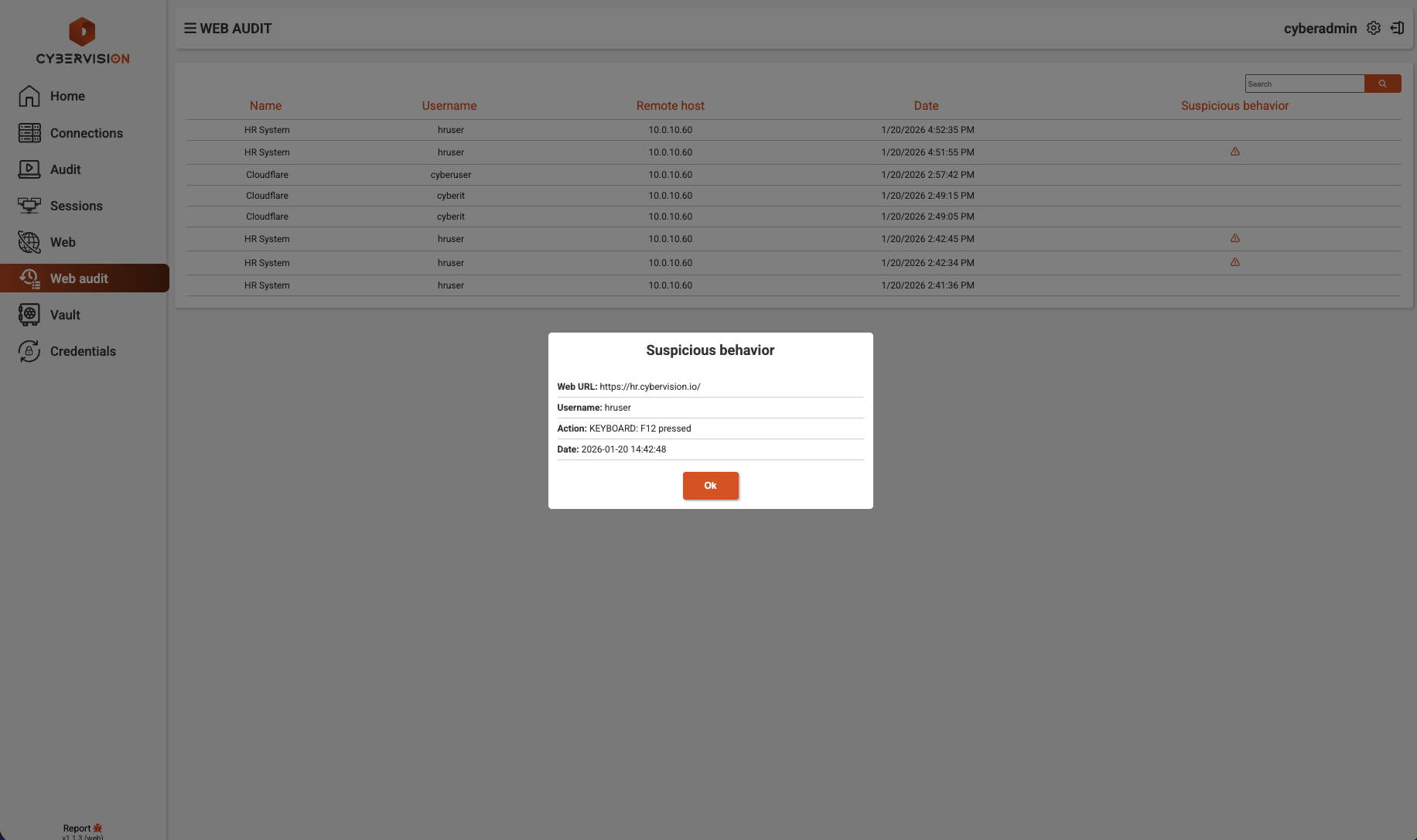
Suspicious Activity Detection
Real-time alerts for suspicious behavior including unauthorized access attempts and unusual keyboard patterns
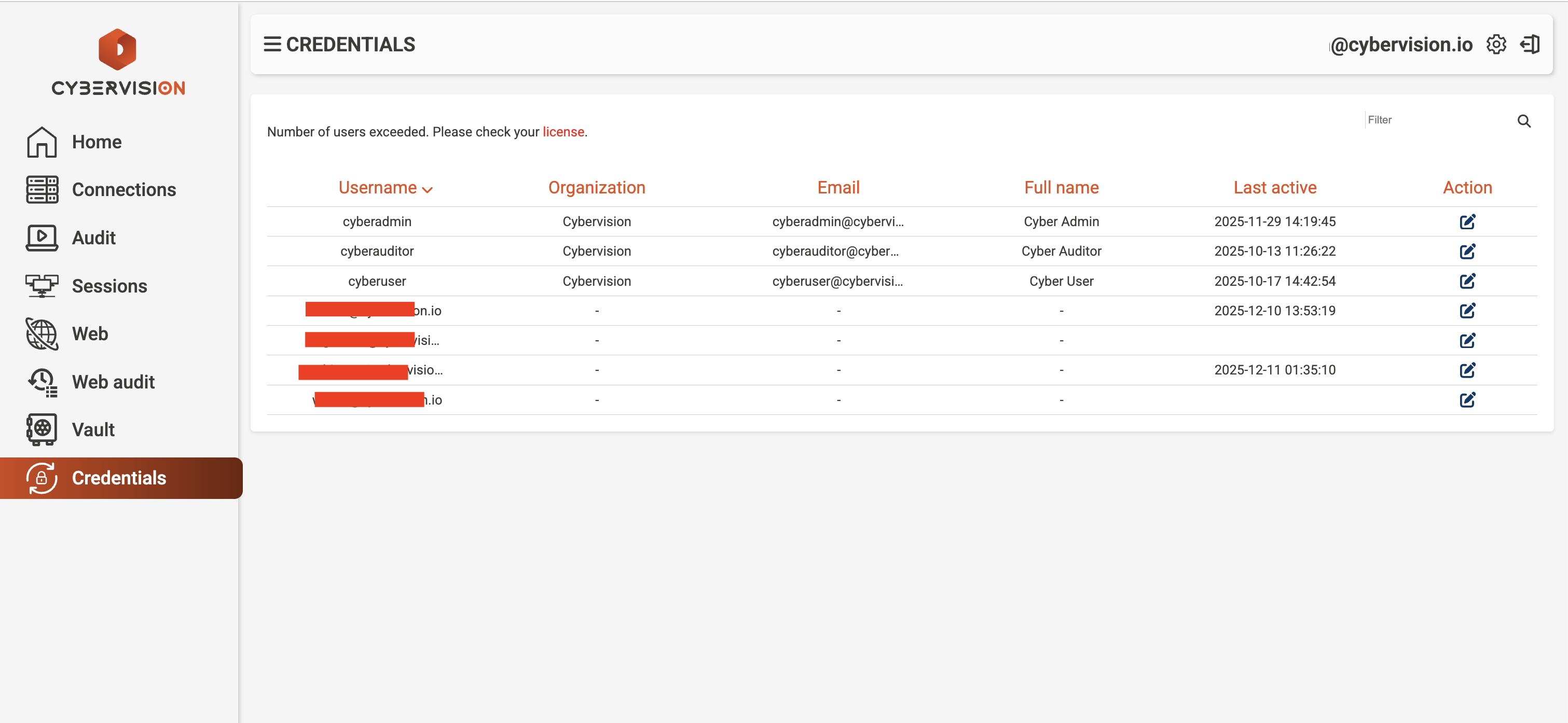
User & Audit Management
Comprehensive user management with detailed audit trails
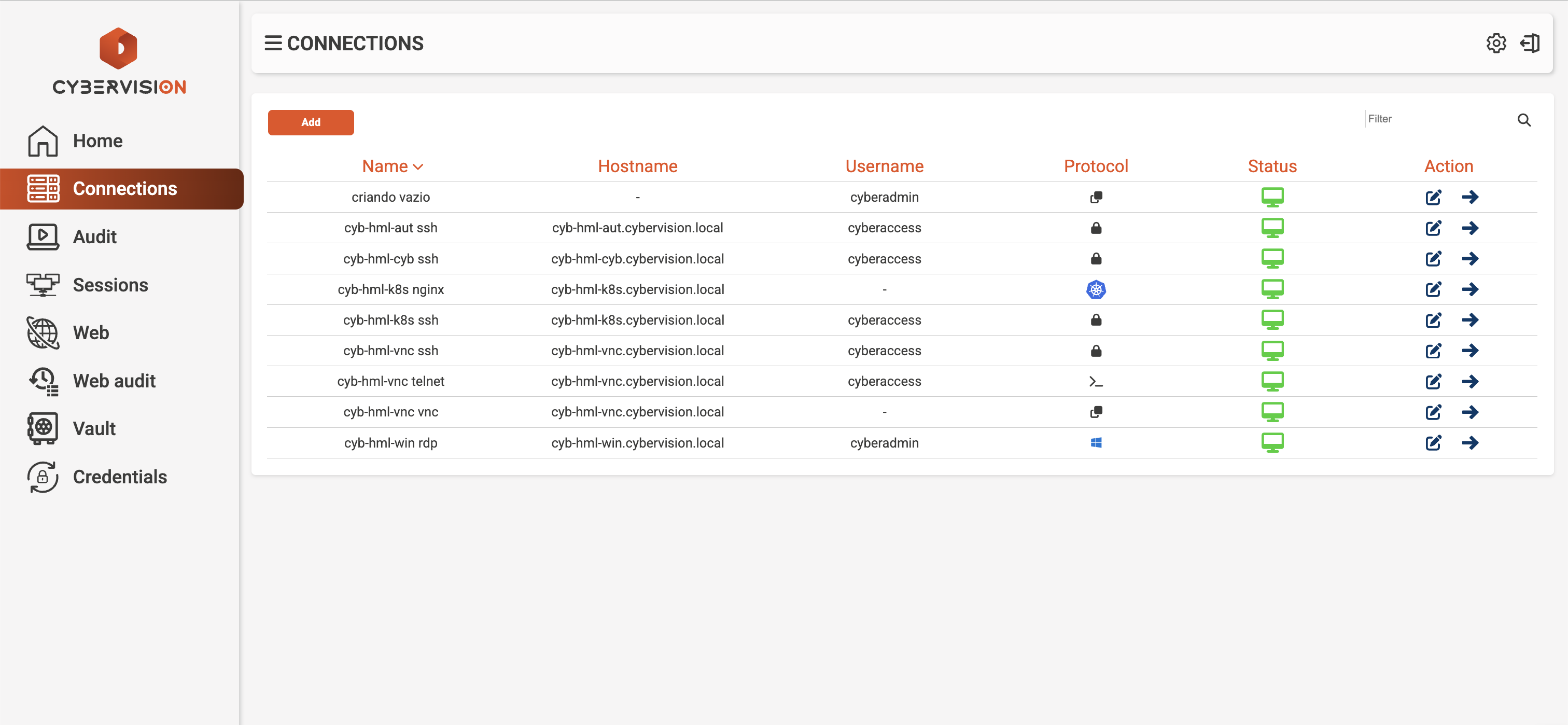
Connection Management
Easy access to all your protected resources in one place